SPIFFE
SPIFFE
SPIFFE is the Secure Production Identity Framework For Everyone. It provides a standard for secure identities using custom X.509 certificates provided to every workload. This removes the need for application-level Authentication and Authorization.
Integration
SPIRE
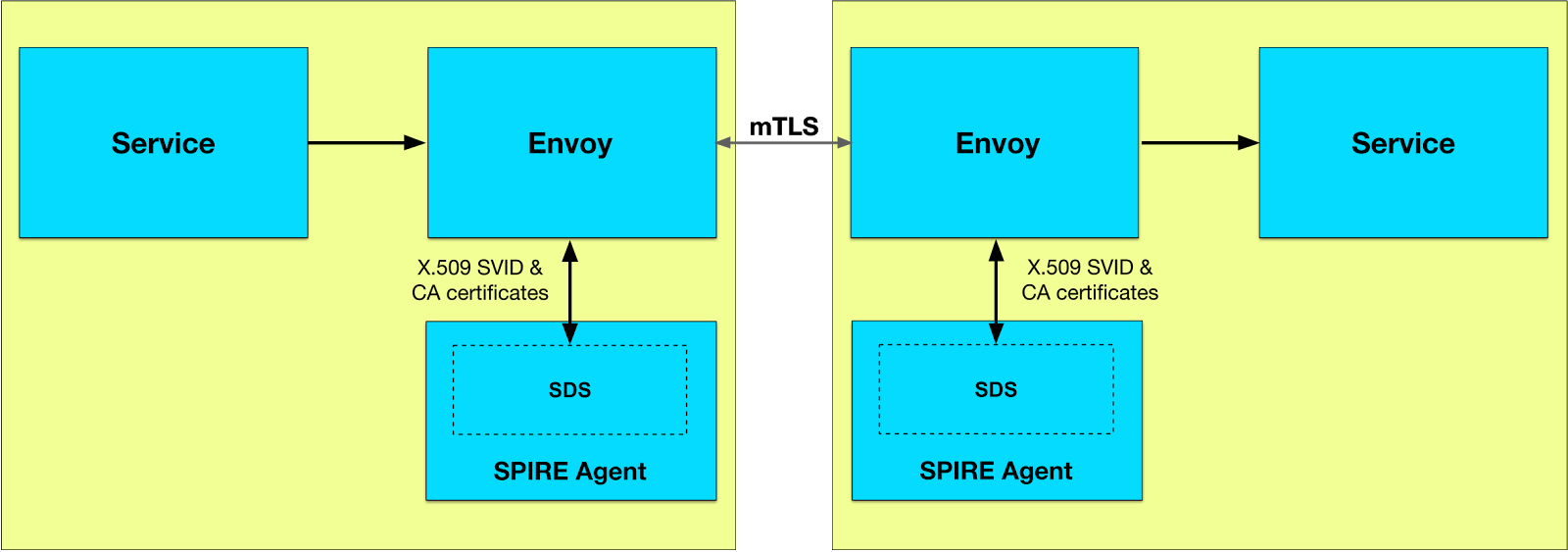
Spire is a SPIFFE implementation. It provides platform and workload attestation, an API for controlling attestation policies, and coordinates certificate issuance and rotation.
Deploying Spire to OpenShift
Initially, spire-agent fails to deploy. If you skip ahead and ignore this, then the /run/spire/sockets wil not be available and pods looking for it as a volume mount will not start.
kubectl describe daemonset --namespace spire
Warning FailedCreate 2m19s (x59 over 4h23m) daemonset-controller Error creating: pods "spire-agent-" is forbidden: unable to validate against any security context constraint: [provider restricted: .spec.securityContext.hostNetwork: Invalid value: true: Host network is not allowed to be used provider restricted: .spec.securityContext.hostPID: Invalid value: true: Host PID is not allowed to be used spec.volumes[2]: Invalid value: "hostPath": hostPath volumes are not allowed to be used spec.initContainers[0].securityContext.hostNetwork: Invalid value: true: Host network is not allowed to be used spec.initContainers[0].securityContext.hostPID: Invalid value: true: Host PID is not allowed to be used spec.containers[0].securityContext.hostNetwork: Invalid value: true: Host network is not allowed to be used spec.containers[0].securityContext.hostPID: Invalid value: true: Host PID is not allowed to be used]
- Spire needs the
hostaccessSCC #447oc adm policy add-scc-to-user hostaccess spire-agent -n spire - SDS support is enabled in SPIRE by default. gm
In other words, SPIRE’s rich methods of defining and attesting services can be used to target the Envoy process, define an identity for it, and provide it with X.509 certificates and trust information that Envoy can use for TLS communication.